Crypto-virus resistent backup

Introduction
Crypto-viruses encrypt your data. If it asks money (a ransom) to decrypt, we call them “ransomware”. They cannot can encypt your SQL Server databases, but because sql data and log files are in use by sqlservr.exe process, they first STOP your sql service, then they encrypt your databases. They also encrypt your DB backups and all other files accessible on file shares. You DO have a backup? Normal backup will NOT protect you from cryptovirus. Because we care for your data and security, we will show you how to protect yourself using free tools. It might take more then a few steps to configure, but it needs to be done only once and it pays off in every way. Read on.
Why “normal” backup is not effective?
Crypto-virus will encrypt your files. Once originals are encrypted, next time your backup runs it overwrites your backup with encrypted files, and both your backup and original files are encrypted, unreadable. Storage replication will also not protect the data for the same reason – an encrypted original will be replicated to the other location too. To prevent that, you need a backup that supports file versioning. With versioning, if original is encrypted and copied to a backup, you could revert to a file version before encryption. But usually the number of versions is limited (eg. to 30), after which the oldest version is deleted.
Second: smart crypto-viruses can flip-flop encrypt the same file repetitively more than 30 times, pushing unencrypted original version out of backup version history. Therefore, you need versioning that will not delete the oldest version until it is really old, e.g. more than month ago, no matter how many times the file is changed during that period. There are multiple ways to solve that. You just need to remember that limited number of versions is not good enough because of repetitive encryption. Cloud backup providers usually offer versioning, but you need to check is the number of versions limited, when repetitive encryption occurs will original file version be pushed-out after N iterations? Others cannot use cloud backup because their data is too big. For example, it takes 6 days to restore 1TB of data with 20Mbit/sec internet connection. Normal local network (LAN) speed is 1 000 Mbit/s and takes only 3h to recover 1TB of data. Compare that to 1 week (or months, depending on data size and connection speed) that would take to recover from the cloud. Cloud makes sense for smal arhives, or smaller part of your archive that is additionally backed-up to cloud, or big archives that can afford to wait a week or month to restore, or restore place is also in the cloud in the same datacenter so between backup and restore location is fast LAN connection. But first check if your cloud is resilient to repetitive encryption.
Third: crypto-virus will look for file shares and encrypt files it finds there. It will look for USB drives (the ones you save your backups to), and encrypt their content too, when you plug them into your PC. You have a backup on a remote file share? If you have write permission, your backup will also be encrypted and your data are not protected from Cryptovirus. You or anybody else (except one special account) should NOT have write permissions to a backup location. That cannot be done with windows permissions, because you are probably administrator on your computer, and therefore the cryptovirus also grabbed “administrator” privileges. And from there he can change windows permissions and encrypt your files.
Then how to be safe, how to protect your most valuable data?
What works?
These are characterists that backup must have to protect your data from cryptovirus:
- backup location YOU CANNOT WRITE to (but backup software can)
- file versioning resilient to repetitive encryption
- automatic (no human to forget to backup)
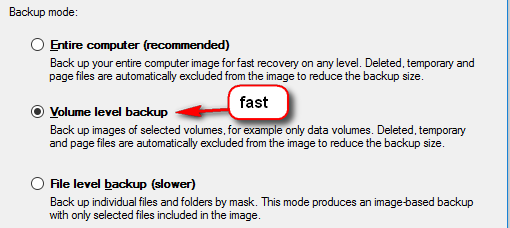
Some enterprise backup systems can do that, but they cost money. Veeam Endpoint Backup is free and easy to configure, but only “Volume level backup” mode is usable, and that backups entire partitions. If you want to backup only specific folders and not entire drive, “File level backup” option is super-slow, and unfortunately unusable. Unless you have a really small number of files. Here is the pic of Veeam Endpoint Backup options one can choose from:
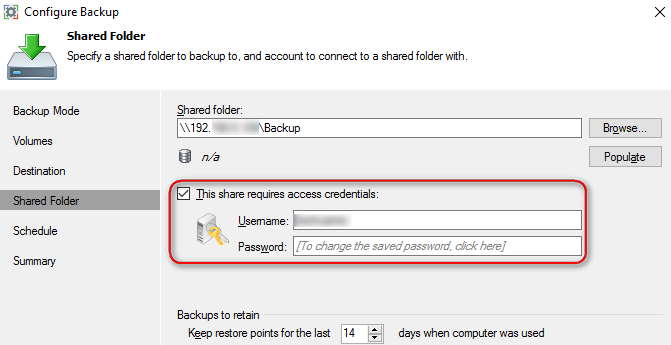
Veeam has neat option to store credentials for accessing remote file share, which greatly simplifies things:
Veeam is super-easy to setup, and if you do not mind backing-up entire partition, it might be a free solution of choice for you.
THE SOLUTION with Free File Sync
What we need
- You need to have a device capable of file-sharing and configuring accounts and permissions. If you do not have such a file server, for home and small business use I recommend Synology 216J. They do not pay me anything, it is just a device that works, has security/permission configuration, and writes at 100 MB/sec. It is very small, silent, reliable and not expensive. Fits 2 x 3.5″ HDD you can put into mirroring mode (RAID1), and has 1Gbit/s network. We will use this one for configuring permissions on file share, but you can do similar with any SMB file server:
- Free File Sync – a free software
- Windows Task Scheduler – you already have that (included in Windows)
Create special “backup” account
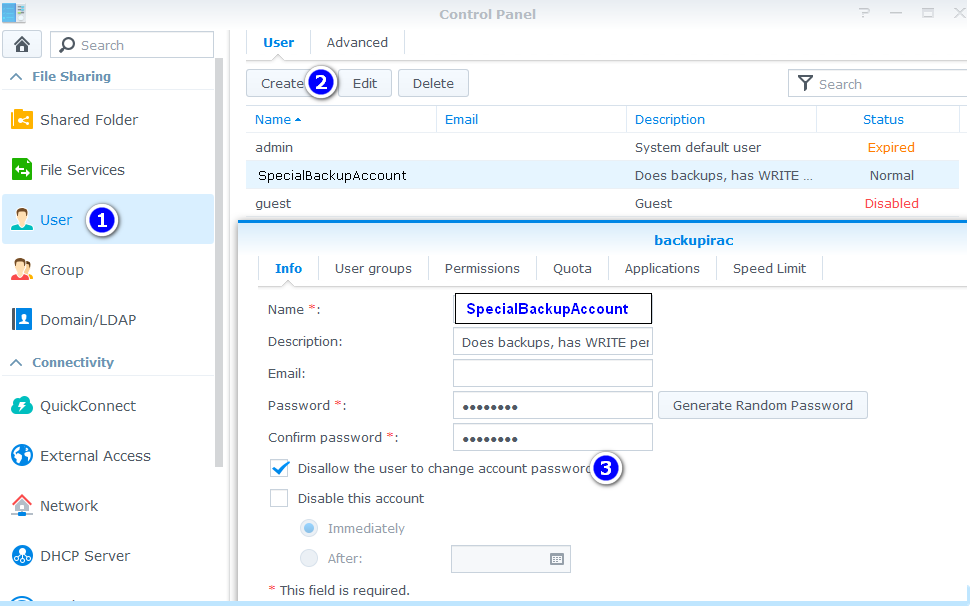
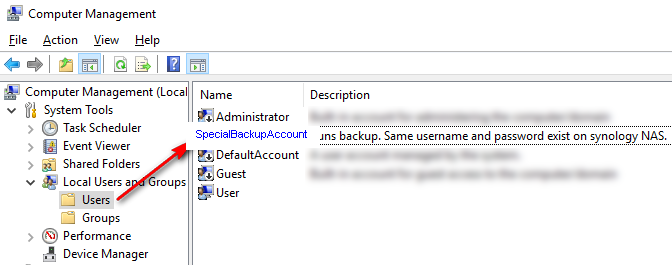
On Synology (or other file server you use) create an account that will be used to write backups. That will be the ONLY ONE with write permissions on backup folder. The name “SpecialBackupAccount” is just an example, you will use some other long unique username and even longer password without any human words in it. You will never use it to login, but the backup software will:
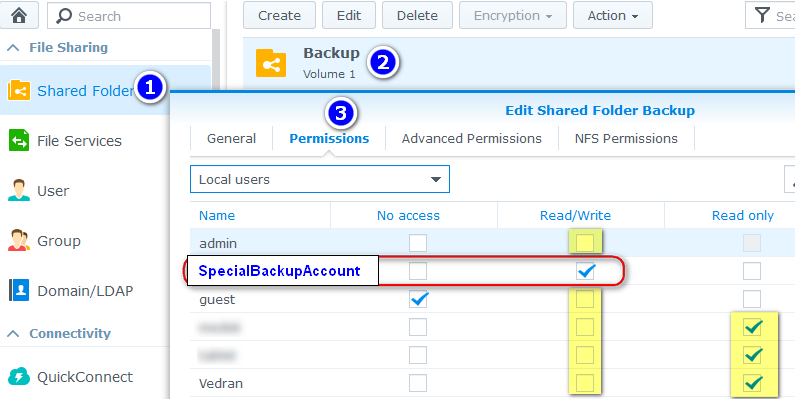
Now configure file share permissions on backup folder for that account. Ensure NO OTHER account has write permissions. Note that my account “Vedran” has read-only permission on backup file share, and is NOT in admin group (cannot write to backup):
If I need to make some changes within backup folder, I do have a separate admin account on that NAS, but I am normally not logged in with that. I never use it from windows machine, and I use it only to login to web interface of NAS and do the changes using web UI file manager.
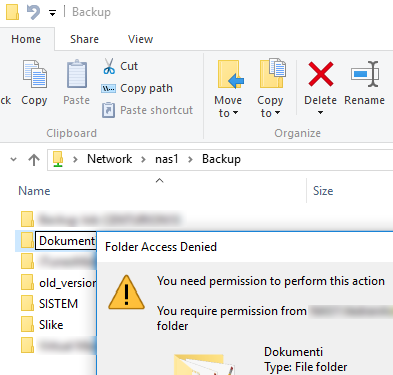
On your PC, with the windows account you normally use (my is “Vedran”) try writing to that remote file share folder. You should get error message like on this picture. If write succeds, you need to fix the permissions. Write error (access denied) is what we want! But you should be able to read the folder without any problem:
Now we are sure Cryptovirus won’t be able to write to a backup location even if it runs under my credentials and even if it has administrator privileges on my PC.
Setup backup using FreeFileSync
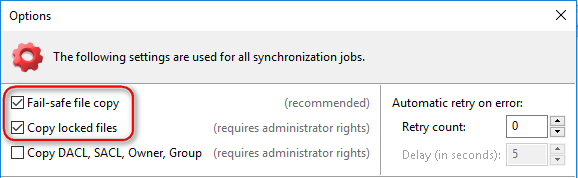
First make sure that “Fail-safe file copy” and “Copy locked files” is checked in Options. That will enable backup of files which are “in use”, and interrupted partial copy will not corrupt destination file:
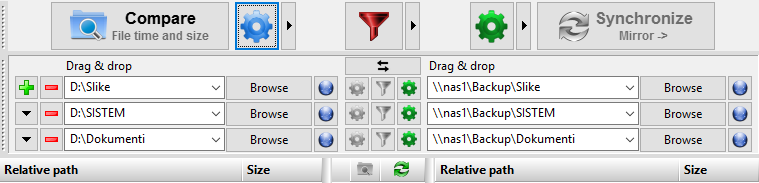
Select folders on your PC that you want to backup, and pair them with remote file share folder on your file server. Here I have 3 folders: Documents, Pictures (Slike), and System. Make sure the type of copy is “Mirror”:
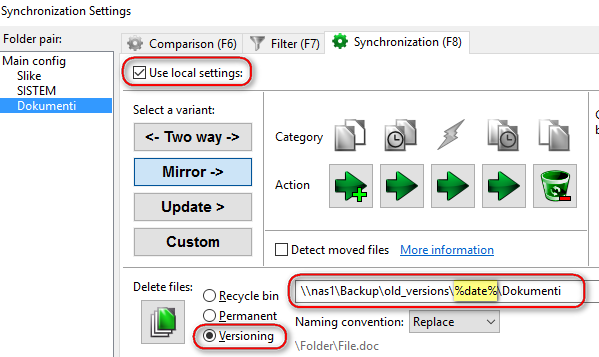
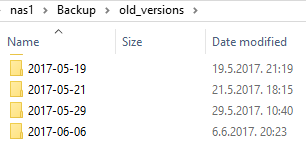
Let’s configure VERSIONING. Under synchronize options, select “Versioning”, and put a “%date%” label under folder path where you want old file verions to be stored, like in the picture. Old versions folder should also be located on protected remote file share folder where your backups are placed:
Do that for all folders you want to backup. I have three of them, and locations for versioning are these:
- \\nas1\Backup\old_versions\%date%\Slike
- \\nas1\Backup\old_versions\%date%\SISTEM
- \\nas1\Backup\old_versions\%date%\Dokumenti
That makes one version per day at most, but it can be configured to a finer level too, eg. hour or minute. File->Save As Batch Job file, e.g. “Backup.ffs_batch”. We will use that file later.
Create account on your PC
Now we create a local SpecialBackupAccount on our PC. We will run backup software on our PC under that account. It must have the same username and password as remote account on NAS we created in previous steps. Put it in “Backup Operators” local windows group, to be allowed to run within a scheduled task. That account will have write access to backup folder on the file share. If you have idea how to remove this step and it works – I would love to hear it:
Schedule the backup
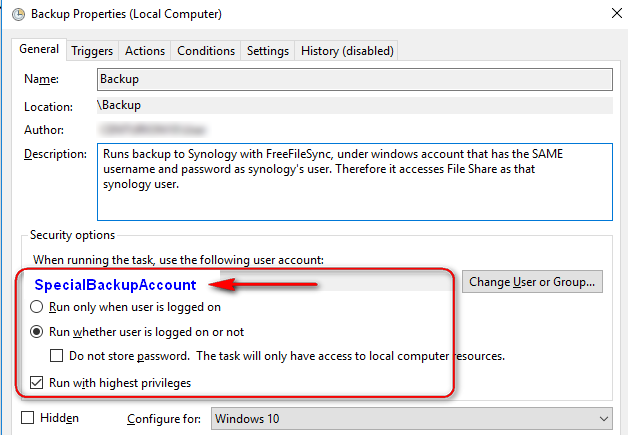
This step is crutial. It not only automates the backup, but also makes backup software running under the only account that can WRITE to backup shared folder. Open Windows Task Scheduler and create a new scheduled task that is running under our newly created local windows account:
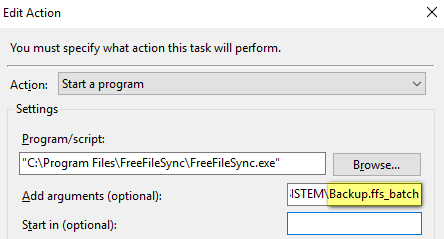
As “action” you need to select FreeFileSync.exe with argument of ffs batch file (*.ffs_batch file) we created in previous steps:
In “Triggers” tab you can create a “Daily” task with “Repeat task every”=”8 hours” for example.
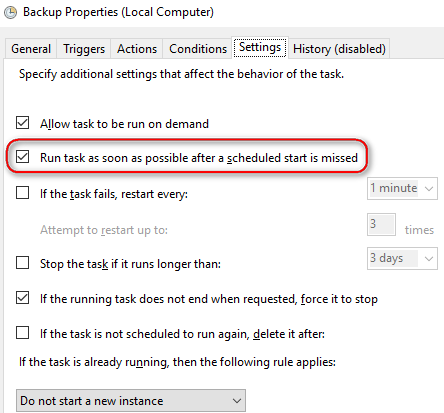
In “Settings” tab of the scheduled task check “Run task as soon as possible after a scheduled start is missed”:
Make it run as often as you need. For me, twice a day is enough, but you can schedule it to run as often as you like.
Verification
Run the scheduled task manually and verify that backup files are created. Change a file and see that the previous version is in “old version” subfolder, similar to this:
You could optionally add a job on NAS to delete versions older than X days, but that can also be done manually on occasion.
That’s it! Enjoy the security.
Conclusion
Ransomware is vicious these days and attacks are more and more frequent. It is possible to protect your data efficiently using free tools and some hardware (file share server) you might already have. Save yourself not only a money for ransom, but also the nervs and time your business is down until bad guys decrypt the files, if ever. Protect yourself. In addition to this method, you can use a versioned cloud backup for specially important parts.
You are more than welcome to comment and share your thoughts on the subject. Add a suggestion or your experience with a Cryptovirus. Let us know did this helped you. Thanks!
LIST OF USEFUL TOOLS
Veeam Agent for MS Windows (formerly Veeam Endpoint Backup) – free is limited to 1 backup job schedule. “Partition Backup” mode can backup one or multiple partitions, works at block-level, and incremental backup detects only changed blocks even in big files. Super-useful if you have big files that changed only a small part, eg. vhdx files of your virtual machines. It compresses and optionally encrypts the backup. Restore is possible at both partition and file level even if backup is done at block level.
Free File Sync – free, no limits
Syncthing – free. Sync between windows, Synology, Android phones, linux, mac, and many more OS and devices. Just pay atention to set “Sender only” for original device that is “master” of the data. If you leave default (Send+Receive) then deletion on other devices will delete files on original device and all devices that can “receive” changes. Put “Send and Receive” on central location (NAS). Optionally: put “Receiver only” on a non-central copy location, so deletions from there won’t propagate, which defines a true “one way” sync. Set versioning to staggered. Great for syncing your phone pics without giving them to google and in original intact state (without recompression or any quality loss). Very powerfull, but not easy to configure, has a learning curve.
Cobian Backup – free, no limits
CloudBerry Backup – fre{“type”:”block”,”srcClientIds”:[“3e539dd2-2b4b-4784-8fb2-886849705ae6″],”srcRootClientId”:””}e version is without compression
Cryptomator – free encryption of cloud drive (dropbox, gdrive etc). You see normal files, cloud provider sees garbage.
APPENDIX – NAS Snapshots
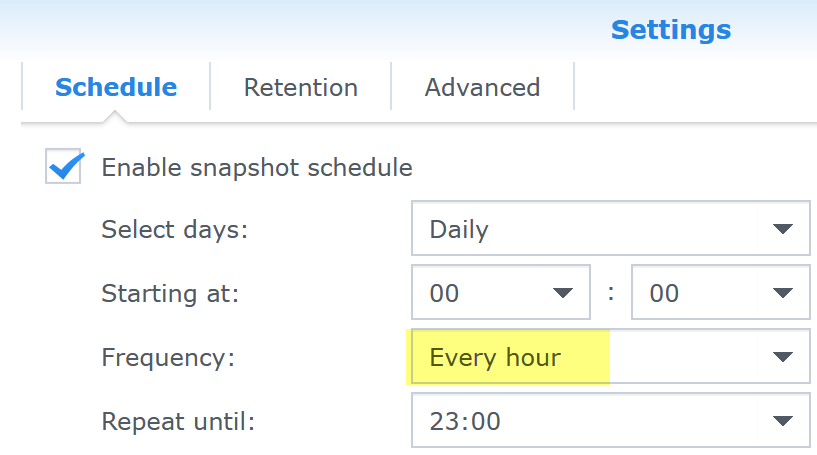
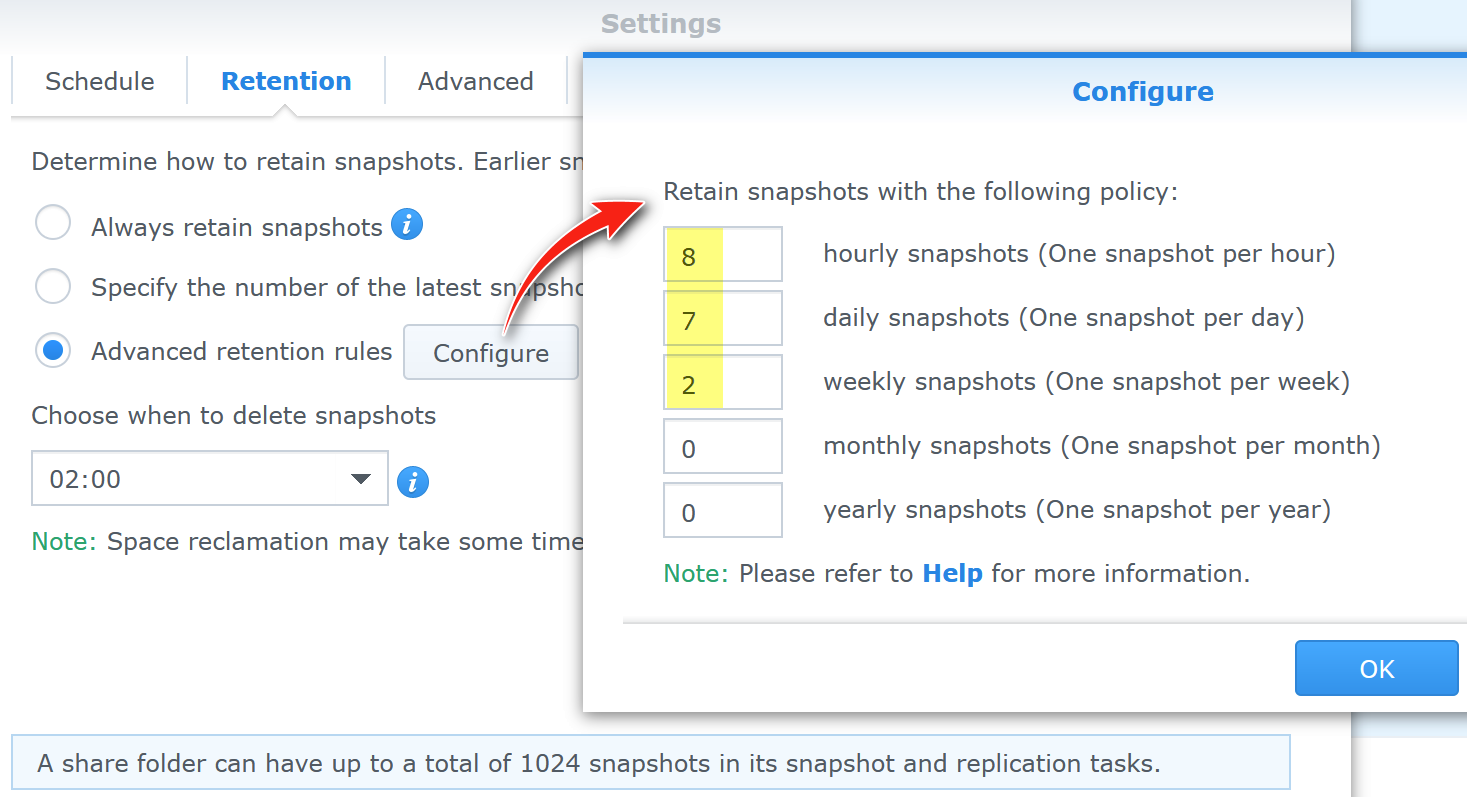
Scheduled NAS snapshots can additionally protect your backup files from cryptovirus ransomware. On Synology NAS you configure them through “Snapshot Replication” app installed through the “Package Center” – we do not have to create any replication copies if we do not want to, just internal snapshots. You can schedule eg. hourly snapshots of the file share with retention of last 8 hourly snapshots, last 7 daily snapshots and 2 weekly snapshots (keeps 14 days old snapshot, one snapshot per day for last 7 days, and last 8 hourly snapshots).
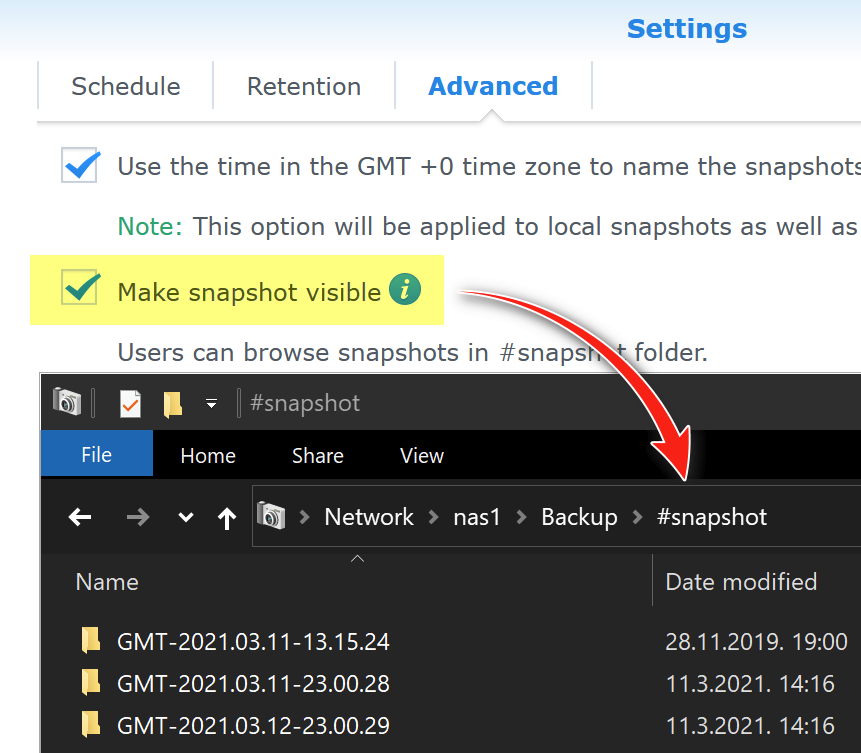
You can also make snapshots visible as a subfolder “#snapshot” inside the file share, if you tick option “Make snapshot visible”:
Snapshots take space only for differences, which is very minimal amount of space and is a highly recommended, inexpensive additional layer of protection from cryptoviruses.
It is also useful to disable SMB1 protocol, for security reasons:
Synology hardening – a quite solid guide:
https://www.itsmdaily.com/how-to-secure-synology-nas-against-exploits-malware-cryptolockers/
Official Synology security hardening guide:
https://kb.synology.com/en-global/DSM/tutorial/How_to_add_extra_security_to_your_Synology_NAS


A friend suggested Cobian Backup as worth considering. It has option to store username and password to use for accessing remote share. With that tool we can skip “creating local windows account” step, and has scheduling built-in, which simplifies the proces. The speed is comparable to FreeFileSync, maybe a bit lower but not much, and it is packed with features. Definitely worth considering.
Hi Vedran, great article, thank you for your effort 🙂
I have noticed typo (word CALL is missing)
it should be:
Often it asks money (a ransom) to decrypt, so we can call them “ransomware”.
Thanks Pera, I really appreciate it. Corrected.
Vedran very informative article. Congrats!
I would like to add my thoughts:
I don’t know exactly how Windows Server Backup (or Win 7 backup and recovery tool) function (especially regarding file versioning), but I think with old good ntbackup tool and any simple pc (yes windows pc) we can achieve the same goal.
1. NTbackup by its design function like file versioning (any new backup is the separate file-entity which doesn’t touch any old one)
2. You only need secured windows pc with allowing only file and printer sharing (it will act as a NAS device). You just have to create special account which will have write and read/execute (not modify) access to backup folder, and that’s it. You can give that credentials to ntbackup or whatever other backup tool on any remote pc.
If you put your credentials as a plain text in bat file -never mind.
Even if virus grab special account password it can do nothing but add new files (it cannot delete or change old files, i.e., backup files).
Maybe I don’t understand file versioning well in concept of backuping. File versioning is -new backup is not allowed to change any previous(old) backup-, right?
If yes, ntbackup tool is capable to do ‘file versioning’.
Ok, ntbackup is not in use any more, but I believe new windows backup tools can do the same (I hope).
Anyway I’m big big fan of Veeam, so I appreciate you approach.
I just wanted to say that we don’t need to afraid of widnows pcs.
Windows pc can be safe as any NAS I would say (with of course properly configured NTFS ACLs and remote access).
Nice idea Damir! To restrict SpecialBackupAccount only to add new files, and cannot overwrite or delete existing ones – really mean! That would require a bit different “add-only” backup process, that handles modifications and deletions with adding backup files. Maybe Cobian backup might do that.
Agree on file server, might be windows, but totally locked for any remote access other than file share.
Moreover we could give SpecialBackupAccount only write permissions without read/execute ones, so it can only add files without any possibility to read them.
Agree with you this approach require a bit different backup procees – it should be created another SpecialBkpDeleteAcc (limited to logon locally only) with purpose of deleting old backup files. With that SpecialBkpDeleteAcc a script #DeleteOldBkps.bat” can be run at regular basis checking free disk space or files older than x days or mix of multiple checking mechanisms and deleting required files.
Writing this I clearly figured out that backup and file versioning are two different techniques linked together for better user data protection.
What about backup on Linux machine?
Ransomware viruses can not operate on Linux, right?
Thanks Coco for the comment. I am not experienced with Linux, but I believe any OS that attackers are interested in can be compromised. Linux might be less interesting for attackers, thus more secure, but for sure nothing is completely secure. Therefore, I believe even on Linux we should have a backup configured similar as described in the post. Synology NAS itself is a linux box. FreeFileSync exists for Ubuntu, Debian, OpenSUSE, even macOS. I see no reason why not to do it on these OS-es too.
Na jednoj sličici ti se u pozadini vidi i ime usera za backup (a nije SpecialBackupAccount :)). Odličan tekst, btw!
Hakirao si me kao zvečku! 🙂 Popravio, hvala!