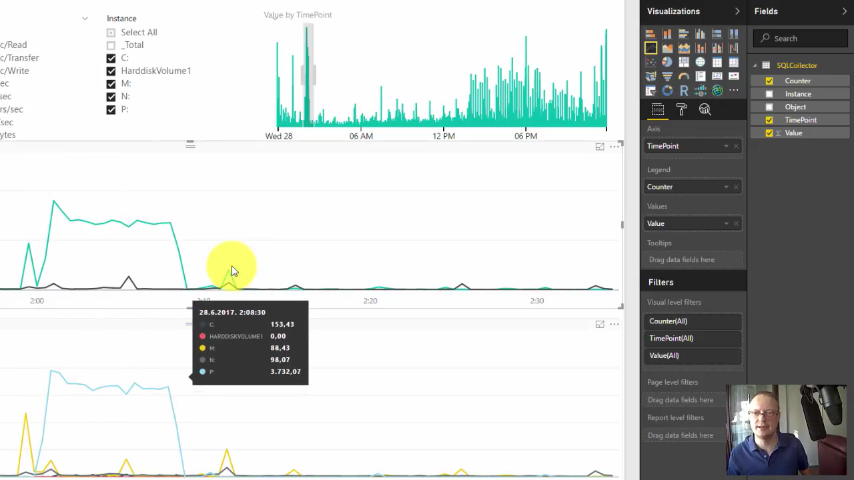
Speaking at Kulendayz 2017
I am honored to be selected to speak in not one but two sessions of SQL Server conference Kulendayz 2017. The topics are “Tuning optional filters” and “Mirror Killer in SQL 2016&2017 Standard Edition”. There are also other great speaks …